Given the global climate, many businesses are looking for ways to tighten their spending belts across several key verticals except one - security.
Gartner projects that information security spending will increase 15% year-over-year to $212 billion in 2025.
When you think about it, this projection makes sense. Operationally, businesses require the internet more than ever—to support global teams, facilitate remote and hybrid work, share important information, and scale their enterprises.
But all this spending will be for naught if teams don’t increase their cybersecurity fluency. In fact, 66% of Chief Information Security Officers (CISO) cite that human error is their organization’s largest security vulnerability this year.
Educating employees on cybersecurity best practices and implementing robust security measures to protect sensitive company data is more important than ever.
Today, we’ll review our top 10 cybersecurity best practices to guard your organization’s data.
Top 10 Cybersecurity Best Practices
Cyber attacks can happen to anyone at any time across any device—mobile devices, tablets, laptops, and desktops.
To help safeguard your organization from these attacks and potential data breaches, we've compiled a list of 10 cybersecurity best practices and other bonus essential cybersecurity awareness tips.
From installing antivirus software to safeguarding confidential information, here are the top cybersecurity awareness resources and tips for your organization.
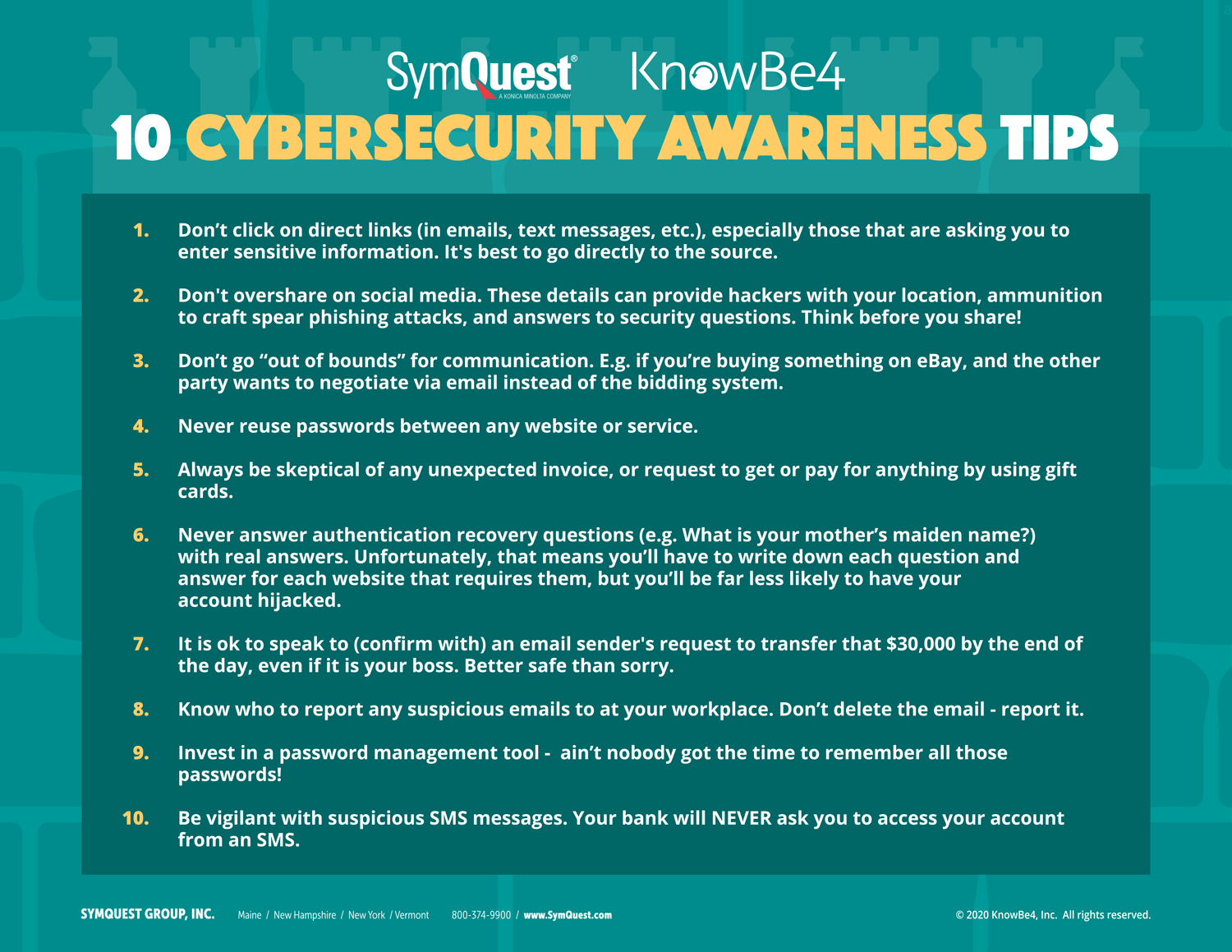
Tip 1: Don’t Click Unknown Links
Clicking on links in emails from unknown senders is one of the easiest ways for hackers to gain access to company data via malware, ransomware, and other malicious code.
Employees should exercise caution and avoid clicking on links unless they are absolutely sure of the sender's identity. A good trick is to look at the sender’s email address. If it contains misspellings, strange symbols, or is someone you don’t know outside of your organization, don’t click on the link and report the email to your IT department.
Links requesting sensitive information or framed as urgent and time-bound are never valid and should be treated as suspicious activity.
Tip 2: Don’t Overshare on Social Media
Social media permeates many aspects of our professional (and personal) lives, especially with the rise of personal branding.
While it has many advantages—connection, thought leadership, networking—sharing too much personal information on these platforms can provide bad actors with valuable data, like clues into how to hack your security questions, or as fodder for social engineering phishing scams.
Avoid posting details such as your location, birthday, children's names, or pet’s names, which are often splashed throughout our passwords, security questions, and more.
It’s also important to limit access to third-party apps and stay up to date on the latest updates and security software for each platform.
Tip 3: Don’t Move Communication Off Designated Site
When working on a designated site, keep all communication within the platform's built-in tools. Moving conversations to email threads, social media messages, or other external channels could put sensitive data at risk.
Designated sites typically have robust security measures in place to protect all parties involved, including encryption, access controls, and communication logs. These features not only safeguard your information but also provide valuable records for future reference, potential audits, or future tests.
To implement this practice, use secure file-sharing platforms, set up proper access controls, and educate employees on the importance of using approved communication channels. Establish clear policies outlining approved platforms and discourage the use of public networks for accessing or sharing work-related documents.
By keeping communication within secure, designated sites, you significantly reduce the risk of data breaches and unauthorized access to confidential information.
Tip 4: Follow Password Best Practices
One of the best practices in cybersecurity is password protection. It’s important to password-protect your critical information. Passwords are instrumental to sound document management and access control policies.
Strong password practices are vital in protecting your organization from potential cybersecurity threats. Ensure your team understands and adheres to the following measures:
- Create unique, strong passwords (mix of words, numbers, and symbols, with 10 or more characters) for different sites and accounts
- Avoid passwords with simple patterns like a birthday, anniversary, or family member’s name
- Never reuse or share passwords
- Utilize a password manager to securely store and manage complex passwords
- Implement multi-factor authentication for an extra layer of security
- Consider passphrases—a sequence of words that creates a phrase—instead of just passwords
- Change passwords periodically to refresh the security
Try to avoid passwords that have memorable (or guessable) mental shortcuts or commonly used passwords. For example, “Pa$$wOrd!1” technically meets some of the standards above, but it leaves a lot to be desired from a security perspective. Be vigilant and aware to protect your accounts.
Tip 5: Be Skeptical of Unexpected Invoices and Payment Requests
Monitor invoices and payment requests carefully, ensuring they align with your records. If you receive an unexpected invoice or payment request, contact the sender directly to confirm its legitimacy. Be wary of requests to purchase services or equipment using gift cards, as these are often associated with scams.
Tip 6: Don't Use Real Answers for Authentication Recovery Questions
Many sites implement security questions as an additional authentication method. However, the answers to these questions are often easily discoverable online. To combat this, use fake answers to safeguard against hackers finding this information elsewhere and compromising your accounts.
Tip 7: Verify Suspicious Emails and Requests With the Sender
While many email platforms can detect and filter spam messages, some may still reach your inbox. If you're unsure about the legitimacy of an email or request, contact the sender directly via a separate email thread, phone call, or in-person conversation. This extra step can help prevent falling victim to phishing scams and protect sensitive information.
Tip 8: Report Suspicious Emails
In addition to verifying emails, it's crucial to report them immediately. By encouraging employees to report suspicious emails, organizations can quickly identify and respond to potential threats that might have bypassed automated security measures. This proactive approach helps neutralize immediate risks and provides valuable intelligence for improving threat detection and incident response strategies.
Employers should establish a clear system for employees to report these emails and provide training on how to identify and report potential threats.
Tip 9: Utilize a Password Management Tool
Modern employees often use multiple online accounts for work, resulting in numerous unique passwords that can be difficult to remember. Offering employees a password management tool will help them securely access different accounts while mitigating the risk of falling into bad password habits, such as using the same password for multiple accounts or writing down passwords.
Tip 10: Don’t Overlook SMS and Text Messages
With people conducting much of their business on mobile devices, it’s important to exercise additional caution regarding security risks associated with SMS and text messages. Be wary of texts from unknown senders or unusual requests.
Legitimate organizations will never ask for sensitive information such as bank account numbers, login credentials, or social security numbers through text messages. As with emails, never click on unknown links or links from unfamiliar sources in text messages.
Additional Cybersecurity Awareness Tips To Implement Across Your Organization
Those 10 cybersecurity best practices were just the tip of the iceberg.
To keep your organization and employees protected from potential threats, consider the following best practices in cybersecurity:
- Install anti-virus software on all devices, including mobile devices and computers.
- Use a virtual private network (VPN) rather than a public network when connecting to public Wi-Fi to encrypt data transmission.
- Regularly update operating systems and software to patch security vulnerabilities.
- Implement physical security measures to protect devices and sensitive information stored on-site.
- Regularly back up important files and data to secure, off-site locations.
- Establish clear policies for personal use of company devices and networks.
- Conduct regular security audits and assessments to identify and address potential vulnerabilities.
All of these tips can help your workforce handle sensitive data with confidence.
Fortify Your Organization’s Cybersecurity Posture
By partnering with trained cybersecurity experts and implementing these cybersecurity awareness tips and best practices, you can significantly reduce the risk of cyber-attacks and protect your organization's sensitive data.
Remember, keeping your cybersecurity up to date is an ongoing process that requires continuous education, vigilance, and adaptation to new threats and technologies.
Reach out to a cybersecurity expert for a security assessment today.





