“When life looks like easy street, there is danger at your door.”
Jerry Garcia may not have been referencing ransomware when he wrote those lyrics but the sentiment perfectly applies. When businesses believe they’re immune from ransomware and forgo proactive cybersecurity, they are overlooking the danger looming around the corner.
Ransomware attacks increased 150% in 2020, and according to a recent report, in 2021 businesses will fall victim to a ransomware attack every 11 seconds with an estimated cost of $20 billion globally.
You don’t have to be an analyst to see the unfortunate trend in the data. Businesses of all sizes have entered the age of ransomware and most of us are unprepared. If you want to prevent your organization from becoming “just another statistic,” it’s imperative to understand what IT resilience is and how your organization can fortify proactive and reactive cybersecurity defense strategies.
Businesses of all sizes can bolster their IT resilience by leveraging a tailored cybersecurity solution designed to avoid costly downtime and ward off sophisticated ransomware attacks.
What is IT Resilience?
Resilience refers to the capacity to recover quickly from difficult and challenging situations.
IT resilience is similar as it refers to a network's capability to quickly adapt and respond to various disruptions - from human error to natural disasters - to mitigate the risk of downtime.
IT resilience is the unified strategy for proactively and reactively responding to cybersecurity threats and ransomware attacks. IT Resilience is a balancing act between a strong proactive defense and a clear reactive process for responding to cyber attacks.
Proactive IT Resilience
Building proactive IT resiliency is no longer optional, it's a business necessity. With the right managed service provider (MSP), businesses can deploy a custom cybersecurity solution that efficiently detects and protects against rising cyber breaches and ransomware attacks. Businesses with even the most basic proactive IT defenses such as multi-factor authentication (MFA) are much more secure than those that remain complacent. For example, the Director of Identity Security at Microsoft stated that accounts are more than 99.9% less likely to be compromised when using MFA.
Businesses that take the time to understand their IT vulnerabilities can prepare a proactive cybersecurity defense strategy to combat ransomware and maintain business-critical operations.
Here are the ways in which businesses can proactively strengthen their ransomware defenses.

Multi-Factor Authentication - A security system that requires multiple login criteria before granting access to a system. This added layer of security ensures that even if login credentials are hacked or stolen, criminals still cannot access the system.
Next Generation Firewall - An advanced cybersecurity tool that controls internet access with additional security features such as intrusion prevention, web filtering, gateway anti-virus, location blocking, and SDWan.
Email Threat Protection - A cybersecurity prevention tool that provides multi-layered filtering to incoming emails. Email threat protection scans and prevents malicious threats such as embedded malware, phishing, social engineering, ransomware, and other spam-type messages.
Network Vulnerability Test - Trusted third-party IT specialists can perform regular network vulnerability tests to identify gaps in cybersecurity protection, ensuring hardened end-to-end security across all networks, devices, and platforms.
Phishing Tests and Security Awareness Training - Employees are prime targets for phishing attacks as they are vulnerable entry points into the business’s larger IT infrastructure. Simulated phishing tests and frequent employee security awareness training are efficient techniques for proactively preparing employees for the inevitable.
Web Filtering - A proactive cybersecurity technology that blocks and restricts end-users access to malicious, hacked, or inappropriate websites.
Encryption - Proactively encrypting employee mobile devices and laptops in addition to multifunction printers and IoT devices ensures the protection of sensitive corporate data.
Phone System Security - Businesses that are still operating internal on-site phone systems are vulnerable to hacks and ransomware attacks which can cause phone bills to skyrocket. Organizations can leverage a custom unified communication solution to deploy a more flexible and secure cloud-based voice system.
Reactive IT Resilience
MSPs report that the average cost of downtime due to ransomware has increased from $46,800 to $274,200 over the past two years. The increased cost of downtime is a bill businesses of any size simply cannot afford. Organizations that leverage a tailored cybersecurity solution ensure their IT infrastructure is built to recover from failure in the event of a ransomware attack.
Businesses that strengthen their reactive cybersecurity defenses with a custom cybersecurity solution can:
- Reduce their overall financial liability.
- Ensure regulatory compliance.
- Efficiently restore business-critical information with minimal disruption.
An end-to-end cybersecurity service is incomplete without a reliable and reactive IT strategy that encompasses a reactive data protection process and a robust business continuity and disaster recovery (BCDR) plan.
Data Protection
Data protection services provide copies and backups of data to allow restoration of lost, deleted, or corrupted data files and/or server images. A custom end-to-end managed IT service will provide data backup services at a frequency that minimizes the risk of data loss.
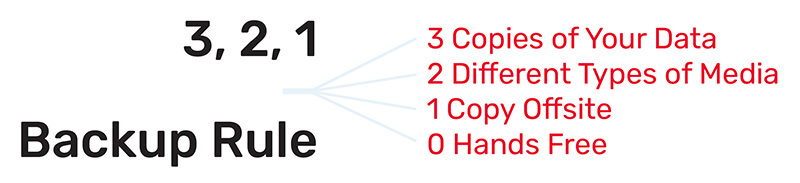
A trusted backup service provider will follow the 3,2,1,0 rule for data backup best practices. The 3,2,1,0 rule states that businesses should have 3 copies of company data. Out of those 3 copies, 2 should be in different types of media, and 1 should be off-site. The 0 refers to a hands-free verified backup without errors.
Business Continuity
A business continuity plan is designed to keep businesses of all sizes operational during or immediately after a disaster occurs. The right business continuity solution provides multiple avenues to continue business-critical operations in the event of a system failure. A business continuity plan should be a written document that includes the organization’s critical functions, supply chain strategy, copies of important records, and employee contact information.
A comprehensive business continuity service provides businesses of all sizes:
- On-premise recovery for a small localized event
- Cloud recovery in the case of a catastrophic event
- Hourly backups for data centers
- Threat vulnerability assessments and processes
- 24/7 proactive network monitoring
- Backup deletion defense capabilities
- Regulatory compliance support
- Quick recovery time
Disaster Recovery
Disaster recovery services provide businesses with a comprehensive reactive strategy to continue operations in the event that the organization’s IT infrastructure is damaged or gone. Compared to a business continuity plan, a disaster recovery strategy focuses more on data recovery, designed to save data that can quickly and efficiently be recovered in the event of a disaster. A disaster recovery solution can range anywhere from recovering a small data set or an entire data center depending on the type of disaster that occurs.
For rapid recovery of data, a robust disaster recovery service encompasses:
- Proactive cloud and local device backups
- Advanced automated disaster recovery software
- Access to experienced IT resilience consultants
- Reliable and consistent recovery time objectives (RTO)
- 24/7 data-driven monitoring for continual IT infrastructure optimization
- Disaster vulnerability assessments and internet security evaluations
- Custom solution architectures including private, public, and hybrid cloud
Keep Your Business Protected with a Tailored Cybersecurity Solution
Businesses need to adopt a forward-thinking mindset in order to proactively protect themselves against ransomware. The organizations that understand the looming danger on the IT road ahead, whether a new ransomware strain, phishing email, or social engineering attack, are better positioned to partner with a trusted managed service provider to implement a custom cybersecurity solution that bolsters proactive and reactive ransomware prevention tactics.





